PlonK Deconstructed 5: Setup
Ben Bencik

In the previous post about KZG, we looked at polynomial commitment schemes. Here, we will explain how to construct polynomials from the values of the arithmetic circuit and discuss what is done in the PlonK protocol setup. This setup calculates common pre-processed input for both the prover and the verifier.
From vectors to polynomials
In the post about arithmetization we considered the values in the circuit in terms of vectors, however, we would like to work with polynomials. We will take as a fact that the polynomial of degree can be uniquely characterized by points. That means any vector of length could be seen as a polynomial in an evaluation form if we pick some evaluation domain. The domain is just a set of unique elements and has the same size as the vector . Think of it this way, the vector represents the coordinate and now we want to pick the points that will represent the coordinate. Let's look at an example with vector and show how picking a domain defines the polynomial. Since , we know right away that we will get a polynomial of degree 2.
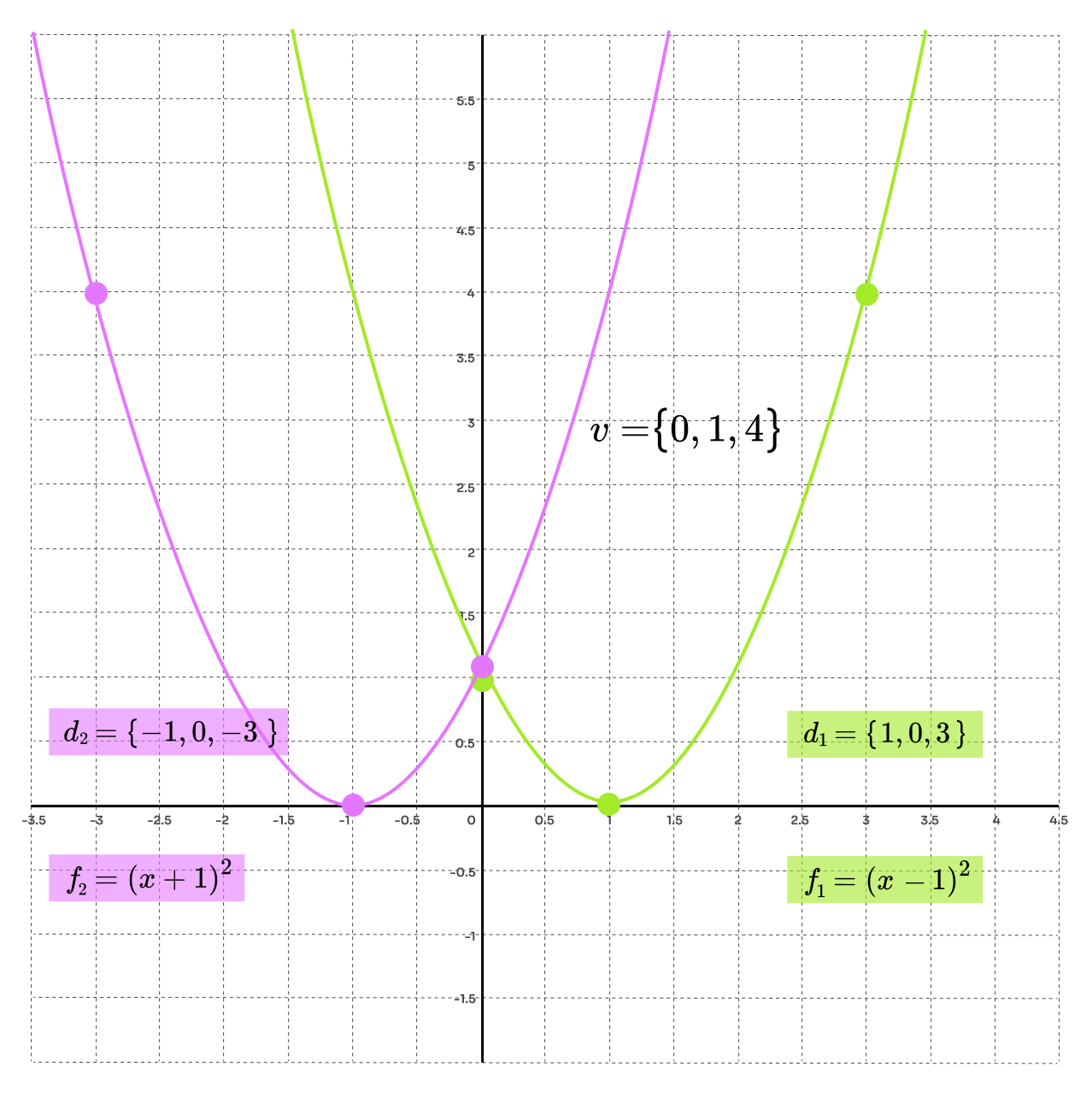
If we pick evaluation domain we get points which define polynomial while the evaluation domain creates a different set of point that define polynomial . By picking an evaluation domain, we get a set of points that uniquely define a polynomial. The domain choice is up to us, and we will use that to our advantage.
All the polynomials we are going to work with are over a finite field . The domain we are going to work with is special because it is generated by primitive -th root of unity as:
Why should we use this evaluation domain? (optional section)
This domain allows for a more efficient representation of certain polynomials. Let's be more specific. Later in the protocol, we will find great use of the vanishing polynomial , which evaluates to zero over the specified domain . The polynomial has all of the roots from $H$ so it can be written as . For large enough , this polynomial gets pretty hard to evaluate. Using , we can write in a much nicer representation. But why does it hold? We just need to show that for :
The size of the domain is , which is the number of gates in the circuit, and the size of field is . In practice, is much much greater than . The size is the security parameter, so the bigger it is, the more secure the protocol becomes. Since all of the elements of are in and it holds that the domain is a subset of the field .
We already know that any polynomial of degree could be represented in evaluation form as a set of points. That is pretty neat, but it turns out that we will need to write polynomials in the standard coefficient form . The problem is that we would like to make KZG commitments where we need to know the coefficient of the polynomial. There are numerous approaches to converting a polynomial from an evaluation form to a coefficient form (interpolating it). We will describe how it can be done using the Lagrange basis because it is easier to explain than the Fourier transform. Given a vector of size we can interpolate it over domain as:
where Lagrange basis is a polynomial that is 1 when and 0 otherwise. For all because in the sum only evaluates to 1 and all other Lagrange bases are 0. This effectively gets us polynomial described by the points:
How does the interpolation work, and what even is ? (optional section)
Take a polynomial created from vector by Lagrange interpolation. For input , only will evaluate to 1, and the remaining Lagrange bases will be zero. Meaning , and that is exactly what we want. For the domain , this mysterious basis could be written as:
When is plugged into , then there is precisely one fraction for which . In that case, the fraction evaluates to 0, meaning the whole product evaluates to 0. If , the consequence is even more trivial because all of the fractions result in , and since , the product of all fractions results in 1. To convince you it is not complicated, look at the example below with the Lagrange basis .

Lagrange basis can have also sparse representation (with fewer coefficient) on the domain as described on page 2 of the PlonK paper.
The PlonK paper also describes the protocol with the Lagrange interpolation, but keep in mind that in practice inverse Fast Fourier Transform (iFFT) is used because it is faster. The whole protocol could be even calculated without interpolation as described in Plonk without FFTs.
Common Preprocessed Input
Since the PlonK protocol runs KZG, all of the parties should have access to the information needed in KZG polynomial commitment scheme . To revise is a prime field, are groups of points on elliptic curves and is efficiently computable group pairing . Lastly are group generators of . Moreover, there needs to be a KZG setup ceremony generating the structured reference string SRS which is public.
Below is summed up the common preprocessed input that is available to both the prover and the verifier. Right now, you do not need to understand how and why it is used, everything will be explained in the following posts.
number of gates in the arithmetic circuit
are needed to create such that the union contains distinct elements. This will be further explained in the round 2.
structured reference string for KZG polynomial commitment scheme
permutation function: you will see how it is constructed in the round 2
selector polynomials: interpolated from selector vectors introduced in arithmetization
permutation polynomials: interpolated from
What do these have in common? They are all dependent just on the structure of the circuit, meaning we could calculate them before the actual execution of the protocol. Now that everything is set up, we can finally start with the first round of the PlonK prover algorithm.
List of the PlonK blog posts:
- 1: Overview
- 2: Arithmetization
- 3: Math Preliminaries
- 4: KZG
- 5: Setup
- 6: Round 1
- 7: Round 2
- 8: Round 3
- 9: Round 4
- 10: Round 5
- 11: Verification
If you have any suggestions or improvements to this blog, send an e-mail to contact@maya-zk.com


